An earlier and more cartel-focused version of this story appeared on Vice Motherboard
An “emerging intelligence report” authored by the Federal Bureau of Investigation and exposed in the 270GB ‘BlueLeaks’ data dump, says organized criminal groups in the Western hemisphere are increasingly using sophisticated encryption to conceal their communications from law enforcement.
The report is titled “Western Hemisphere Transnational Criminal Organizations Very Likely Expanding Use of Increasingly Sophisticated Communications, Impeding Investigations.” It was published in February and co-authored by FBI field offices in San Diego, Tampa, and New Orleans.
This document is one of at least five law enforcement reports exposed by the data dump that deals with the challenges faced by investigators when criminals communicate via encrypted platforms.
Beyond more widely adopted end-to-end encrypted messaging apps like Signal, WhatsApp, Wickr, Telegram, and Kik, the FBI said transnational crime groups are using ‘hardened encrypted devices’ and other more sophisticated platforms, “impeding law enforcement’s ability to intercept communications.”
Based on reporting from three FBI human sources, one Drug Enforcement Administration human source, and one law-enforcement source, the FBI made this assessment with high-confidence.
Both the FBI and the DEA declined to comment for this story.
Takedown ‘Sans Précédent’

The revelation of this document comes in the wake of the ‘unprecedented’ takedown of the EncroChat “encrypted phone network widely used by criminal networks” by a Franco-Dutch-led, law-enforcement operation made public on July 2 by Europol and the European Union Agency for Criminal Justice Cooperation.
According to a Vice news report published shortly after the EnroChat press conference, this takedown would not have been possible without a sophisticated cyber-exploit that French law enforcement is keeping secret under threat of criminal prosecution, according to the French press release.
As of early 2020, the joint press release from Europol and Eurojust alleges: “EncroChat was one of the largest providers of encrypted digital communication with a very high share of users presumably engaged in criminal activity. User hotspots were particularly present in source and destination countries for cocaine and cannabis trade, as well as in money laundering centres.”
Europol, Eurojust, and the public prosecutor of Lille – the interregional jurisdiction of France that has authority over the EncroChat case – all declined comment beyond the press package that accompanied the July 2 news conference.
But EncroChat has been on U.S. law enforcement’s radar since at least November 2018, according to an unclassified case citation that was marked DEA sensitive and also law-enforcement sensitive in the FBI report.
Narco Phone
Specifically, the DEA identified a Mexican transnational criminal organization (TCO), linked to the Sinaloa Cartel, that was acquiring EncroChat phones in Europe for its internal communications and to correspond with a “Canada-based trafficking associate, according to a human source with direct access.”
As of August 2019, this Mexican TCO was engaged in the “trafficking of precursor chemicals from China and India and fentanyl to the United States, according to a human source with direct access.”
And according to intelligence collected in October 2019, the FBI report again cited the use of EncroChat in an investigation involving a senior Sinaloa Cartel leader “to communicate and facilitate criminal activity, according to a human source with direct access.”
EncroChat Decrypted
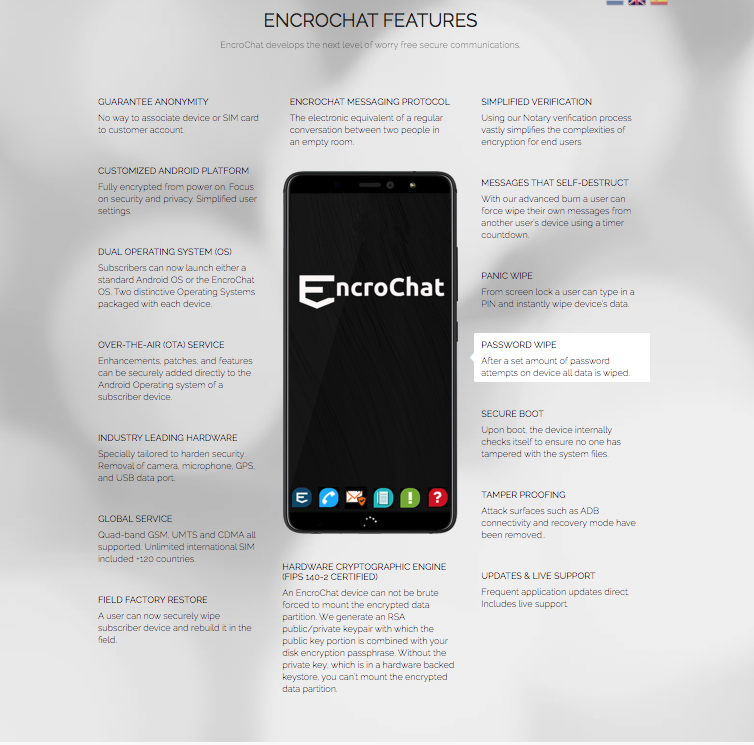
In a report footnote, the FBI describes EncroChat as an “encrypted device and platform that maintains two operating systems on the phone and operates like a typical phone that advertises complete anonymity, with options for a panic wipe by entering a one-time personal identification number from the log-in screen, tamper proofing, messages that self-destruct, and additional security features.”
Operational since at least 2015, per Whois website domain registration records, the EncroChat network enabled some 60,000 users worldwide to acquire modified Android devices, with no device or sim card association to their customer accounts, according to the National Crime Agency, the U.K.’s top law-enforcement body.
The NCA press release says they had been sharing intelligence with international law enforcement agencies to target EncroChat since 2016. EncroChat’s flagship product, the ‘EncroPhone,’ was a retrofitted BQ Aquarius X2 Android model. This handset was released in 2018 by a Spanish electronics company, according to leaked investigation documents obtained by Vice.
Sim cards used in these phones were made by Dutch telecom firm KNS, according to Vice reporting. EncroChat also stripped these handsets of their camera, microphone, GPS, and USB terminals, and installed proprietary encrypted messaging programs on them, which routed texts through their own servers, “located offshore” in their datacenter, according to an archived EncroPhone webpage.
EncroChat’s web marketing collateral also claimed their servers “never create, store, or decrypt keys, message conversations or user data.” Once stripped and reengineered, EncroChat sold these cryptophones for roughly EUR 1,000 each “at international scale” and offered subscriptions with worldwide coverage for EUR 3,000 a year.
Operation Emma 95
This investigation launched in 2017 was spearheaded by French police, known as the Gendarmerie. The operation was codenamed “Emma 95” in France, according to the French press kit.
Technical research conducted on EncroChat phones seized by French police revealed that the “encrypted communication solution, not declared in France,” actually hosted some of its “offshore” servers there, according to the French press release.
The servers’ location thus gave French authorities legal jurisdiction to collar the investigation. Partnering first with Dutch authorities, and then EUROPOL, French cyber cops infiltrated the clandestine telecomm network via an ambiguous ‘technical device,’ according to the French press release.
An EncroChat associate described this so-called device to Vice, as a “mass hacking operation.”
Key to the development of the technical device that enabled the hack was research conducted by the Institute for Criminal Research of the National Gendarmerie (IRCGN), according to the French press release.
The IRCGN is the French coordinating entity of an organization known as the CERBERUS project, which is a partnership between the Forensic Laboratory of the Gendarmerie, the Netherlands Forensic Institute, and University College of Dublin to combat child abuse by beating encryption to “unprotect systems.”

This institution was a catalyst for the development of the technical device and “accelerated the the research by the IRCGN concerning these phones,” according to the French press release.
But it took nearly a year to operationalize the exploit, as the press kit says the CERBERUS project’s involvement in the project started in early 2019. The Joint Investigative Team formed by France and the Netherlands, which presumably gave law enforcement officials bilateral legal authorization to comb through unencrypted messages and unmask users, was not formally signed until April 10 of this year.
“Indeed, the CERBERUS project has contributed to the EncroChat hack,” said Gerdarmerie Major Lionel Prat, a CERBERUS project manager. “The research carried out within this framework provided a big boost to certain components of the EMMA 95 operation,” he added.
Despite billing itself as a research organization focused on breaking or cracking passwords, the CERBERUS project “is a very vast project,” notes Major Prat.
“We are looking for all the ways to access the data in clear-text, not necessarily by breaking the encryption or looking for the key/password,” said Pratt. “It is about the search for vulnerabilities, we are no longer in the theme of breaking but the search for ways to ‘bypass’ the encryption.”
Citing French “national defense secrecy” laws that repress disclosure of elements relating to the technical device, Major Prat declined to comment further.
But an unnamed EncroChat associate told Vice that the team discovered malware on the cryptophones. This malware was “specifically created for the X2 model,” according to Vice.
Ultimately, French, Dutch, and other European law enforcement agencies were able to surveil communications from “more than a hundred million encrypted messages” exchanged between Encrochat subscribers in real-time. This has led to over a thousand arrests across the UK, Norway, Sweden, France, and the Netherlands this year, according to Europol.
In the aftermath of the sweep, Dutch police said the “advanced and internationally coordinated operation has the same effect as a serious earthquake for organised crime.”
The EncroChat breach has given law enforcement “insight in an unprecedented large number of serious crimes, including large, international drug shipments and drug labs, murders, thrashing robberies, extortions, robberies, grave assaults and hostage takings. International drug – and money laundering corridors have become crystal clear,” said the Dutch press release.
Anatomy of an Exploit
A well-known executive in the digital forensics industry who requested anonymity speculated that the exploit deployed by French cyber cops was an over-the-air attack like the type that has made Israeli spyware firm, NSO Group, infamous.
“This sounds like some vulnerability that allowed getting into the device over the air and then once you run on the phone via remote code execution, you basically control it and can get all the data both stores on the device and in transit, so you basically bypass the peer to peer encryption as you run on the device itself.”
Deploying this OTA attack via cyber-exploits that require targets to click on one or zero clicks, NSO’s ‘Pegasus’ exploit has been linked in media reports to the phone hacking of drug lord “El Chapo,” slain Saudi journalist and alleged Qatari intelligence asset Jamal Khashoggi, Amazon chief Jeff Bezos, and most recently by Vice, to politicians in Spain.
Via a spokesperson, NSO denied all involvement in the Bezos hacking and the Khashoggi affair. “NSO software is operated in line with our industry-leading governance policies solely by authorized government agencies to fight terror and serious crime, and protect public safety,” said the spokesperson.
As far as the EncroChat hack is concerned, Major Prat also noted, “I don’t know the technical details of Pegasus, so I can’t speak to that.”
Nevertheless, the OTA attack vector indeed seems possible, as the Encrophone.com website, which marketed EncroChat’s “worry free secure communications,” advertised an OTA service that enabled “enhancements, patches, and features” to be “securely added directly to the Android Operating system of a subscriber device.”
Meanwhile, cybersecurity expert Richard Stiennon, the chief research analyst for infosec firm IT-Harvest, posited that EncroChat’s Dutch sim card vendor may have cooperated with authorities and helped them infect the cryptophone network with the CERBERUS exploit.
An EncroChat associate expressed Stiennon’s exact hypothesis to Vice, in fact. But the forensics executive discounted this possibility. “I don’t think the telecom company had any significant involvement,” he said.
Satellite Radios and Other Clandestine Comms
Beyond EncroChat, the FBI report also cited two other cases were sophisticated communications were used by drug traffickers. Intelligence collected by the FBI in September 2019 revealed that a go-fast boat captain used Garmin Inreach Explorers, a handheld satellite device that allows two-way texting and email communications with any other mobile number or email address.
Except, these Garmin devices were “altered by two hackers to communicate with land-based individuals during maritime drug trafficking operations, according to a human source with direct access,” the report said.
The FBI has corroborated this particular source’s information for more than a decade, added the report. The FBI also noted that, “Both traffickers and crewmembers felt safe using this new method of communication as it was done via satellites and harder to trace.”
Additionally, it is well-known in law-enforcement circles, that satellite phones are popular operational security for maritime drug-trafficking communications.
Lastly, intelligence collected by the FBI in November 2019, TCOs engaged in maritime drug trafficking out of La Guajira, Colombia, in the North East region of the country facing the Caribbean Sea, communicated in on phones “equipped with hacker software.” This intelligence came from a “human source with direct access,” according to the report.
The FBI report said that an “unidentified La Guajira hacking group provided this modification service to TCOs, charging US $3,000 per 6-month phone contract.”
FBI Assessments
Given the intelligence collected, the FBI assesses that TCOs in the Western hemisphere “very likely will attempt to move much of their communications regarding criminal activity to some level of publicly available encrypted applications in the near term.”
In the long term, the FBI assesses Western hemisphere TCOs will likely “recruit their own technical experts to develop in-house encrypted systems for their exclusive use, including devices and servers,” according to the report.
Going in-house will enable crime organizations to “maintain complete operational security over their communications, rendering traditional law enforcement interception capabilities ineffective,” said the FBI.
The FBI also cites the significant decline in transactional data from “traditional communications judicial returns or positive responses to judicial inquiries” for encrypted messaging companies indicating accounts are held by crime organizations, as signs that Western TCOs are migrating to end-to-end encrypted platforms.
Code of Silence

Following the EncroChat takedown, Vice notes that upstart, Scottish cryptophone company Omerta, which is the word used to denote the Southern Italian code of silence, and which advertises the “military-grade encryption” of its devices on its website homepage, has been advertising directly to Encrochat’s old customers.
Craig Buchan, the 42-year-old founder and CEO of Omerta and a British special forces veteran, is critical of EncroChat’s ‘mediocre’ handset and toolset, “which are rather normal within enterprise IT environments.”
The Omerta chief also cites relatively higher EncroChat employee headcount as a reason for the network’s downfall. Buchan speculates that their inability to keep tabs on all of their personnel enabled French police to compromise the network with the help of an insider.
Despite being a family-run operation consisting solely of himself and his partner, Sharon, which heightens key-man risks for Omerta’s operational resilience, Buchan believes his ‘tight-knit unit’ will actually help his company avoid EncroChat’s possibly internal governance meltdown.
“Our future plans involving headcount growth involve family members and even then, this still makes us a small outfit of four. So, in short, I’d notice an undercover agent by merit of headcount,” said Buchan.
But cybersecurity expert Stiennon noted that solutions like Omerta and EncroChat have proven unattractive for clandestine networks because they inherently represent a single point of failure.
Buchan disputes this categorization of his product. “When you describe a single point of failure, I feel you either do not understand the concept or have failed to understand Omerta,” he said. “We operate a strategy of ‘distributed risk and reduced impact,’ as our approach to product delivery. I am very satisfied it works.”
Specifically, Buchan cites a key difference in his ‘approach’ to security relative to EncroChat. While Buchan’s team itself is highly concentrated, Omerta’s “business model is more akin to Dell,” operating more like an IT provider, as opposed to a telecoms specialist, he said.
“We provide hardware pre-configured with third-party applications. Using my experience in and knowledge of IT and encryption, I curate applications which enable our customers to benefit from a secure handset and secure communications.”
“This approach benefits our customers because applications are built by specialist providers, so, based on the division of labour, we pick the best company to deliver the best application,” said Buchan.
Regardless, Stiennon cautions: “No matter the level of security, never trust a system that caters to a large population of bad actors. Such target-rich environments will be inevitably be targeted by law enforcement and the intelligence community.”
Intel Honeypot All Along?
Meanwhile, a source, who requested anonymity, and who is affiliated with Dutch intelligence told Shadow Banker that EncroChat was a French and British intel honeypot all along.
The source said: “‘Its pretty simple these offers of encrypted phones are set up by the intelligence services after the example of the General Intelligence and Security Service and Dutch Military Intelligence and Security Service in the Netherlands. Later repeated by the U.S. in Mexico and now finally by the UK’s and France’s military intelligence services.”
“That means that any evidence collected, will only be transferred to the intelligence services of the police, who know NOTHING about the realities in the field, except for what the intelligence services want them to know to build a criminal case.’ It is not exciting to know about the technicalities, as everything was and is controlled by the intelligence services, to target terrorism-organized-crime nexus and not solely organized crime.’

http://dreadytofatroptsdj6io7l3xptbet6onoyno2yv7jicoxknyazubrad.onion/post/1a27da143890eecee484/#c-1911011df9293b4bb0
Hello there, just became aware of your blog through Google, and found that it is truly informative. I am gonna watch out for brussels. I’ll appreciate if you continue this in future. Numerous people will be benefited from your writing. Cheers!|